- John The Ripper 0 Password Hashes 1 Left Hand Grips
- John The Ripper 0 Password Hashes 1 Left Hand Piano
Practice ntds.dit File Part 6: Password Cracking With John the Ripper – Wordlist
A previous session can be retrieve thanks to john.rec file. To restore a session, issue: $./john -restore Retrieve cracked passwords. To retrieve cracked passwords (in this example, no password has been cracked, session has been aborted): $./john -show /etc/shadow 0 password hashes cracked, 2 left. If you don't want to use the default password.lst file of JohnTheRipper, just specify the path to the new file using the -wordlist argument: john -wordlist=password.lst protectedpdf.hash. As final recommendation, the tool offers to crack a lot of files, so you may want to read the documentation of the library. Jan 26, 2017 john -format=NT -show hashfile.txt 634 password hashes cracked, 2456 left. If you go through your hashes in hashdump format and you see a lot of Administrator::500.
After password cracking examples with hashcat, I want to show you how to crack passwords with John the Ripper (remember we also produced hashes for John the Ripper: lm.john.out and nt.john.out).
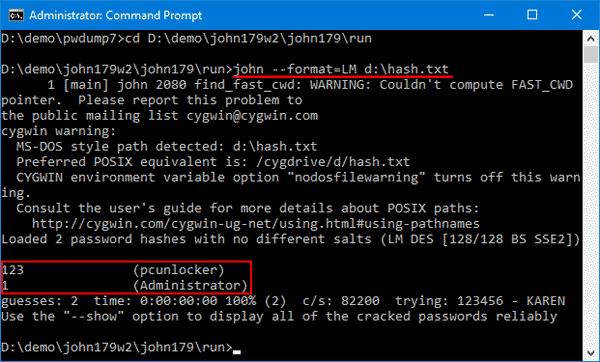
First we use the rockyou wordlist to crack the LM hashes:
Option –wordlist specifies the wordlist to use, and option –pot specifies the pot file I want to create/use.
Output:
And then we use option –show to display the (partially) recovered passwords:
Output:
Cracking NTLM hashes is done with a similar command, it’s just the name of the files that changes:
Output:
John The Ripper 0 Password Hashes 1 Left Hand Grips

And then we use option –show to display the recovered passwords:
John The Ripper 0 Password Hashes 1 Left Hand Piano
Output: